Git SSL Certificate Problem Caused By Self Signed Certificates
Category : How-to
 It’s never been easier to set up your own Git server to host your own git repositories for your projects. Thanks to people like the folks over at GitLab you can be up and running in no time at all.
It’s never been easier to set up your own Git server to host your own git repositories for your projects. Thanks to people like the folks over at GitLab you can be up and running in no time at all.
If you host something like this yourself, you’ll probably have entered the world called self signed certificates. These are SSL certificates that have not been signed by a known and trusted certificate authority. There is no security concern using a self signed certificate, the level of security will be similar to a paid for certificate, the problem is that your commuter won’t know that it can trust the certificate. You may have seen this error in a Web Browser, such as Chrome:
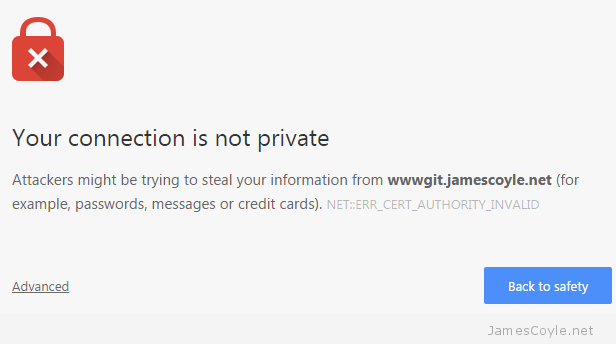
With Git, however, you’ll get an error from the git command line tool similar to the below:
$ git clone https://wwwgit.jamescoyle.net/test/test-project.git Cloning into 'test-project'... fatal: unable to access 'https://[email protected]/test/test-project.git/': SSL certificate problem: unable to get local issuer certificate
The preferred method of dealing with this error is to add the Certificate Authority’s signing certificate as a trusted Certificate Authority on your computer.The way to do this differs depending on your OS and is out of scope for this post.
There are two Git specific methods of forcing Git to accept the self signed certificates, which don’t require you to import the CA certificate to your computers Trusted CA store:
Turn off Git SSL Verification
You can stop the Git client from verifying your servers certificate and to trust all SSL certificates you use with the Git client. This has it’s own security risks as you would not be warned if there was a valid problem with the server you are trying to connect to.
That said, it’s the quickest and easiest fix for a non trusted server certificate. Simply run the below git command on your Git client.
git config --global http.sslVerify false
Tell Git Where Your Certificate Authority Certificates Are
Another option is to point your Git client towards a folder that contains the Certificate Authority certificate that was used to sign your Git server’s SSL certificate. You may not have one of these if you’re using Self Signed certificates.
Save the CA certificate to a folder on your Git client and run the following git command to tell your Git client to use it when connecting t the server:
git config --system http.sslCAPath /git/certificates
 Creating a template from an OpenVZ container is a very manual process. My biggest problem is that you have to have root access to the Proxmox hardware node in order to create a tar from the root of the CT. See
Creating a template from an OpenVZ container is a very manual process. My biggest problem is that you have to have root access to the Proxmox hardware node in order to create a tar from the root of the CT. See 

 Good news: installing Grails from source is easy-peasey on Windows! Before you get started, you’ll need to have git and a JDK installed.
Good news: installing Grails from source is easy-peasey on Windows! Before you get started, you’ll need to have git and a JDK installed. With Git you are able to define file exceptions to exclude certain files and folders from git repository commits. You can create files which contain a list of patterns which git will check against on each git add and ignore any matching files.
With Git you are able to define file exceptions to exclude certain files and folders from git repository commits. You can create files which contain a list of patterns which git will check against on each git add and ignore any matching files.